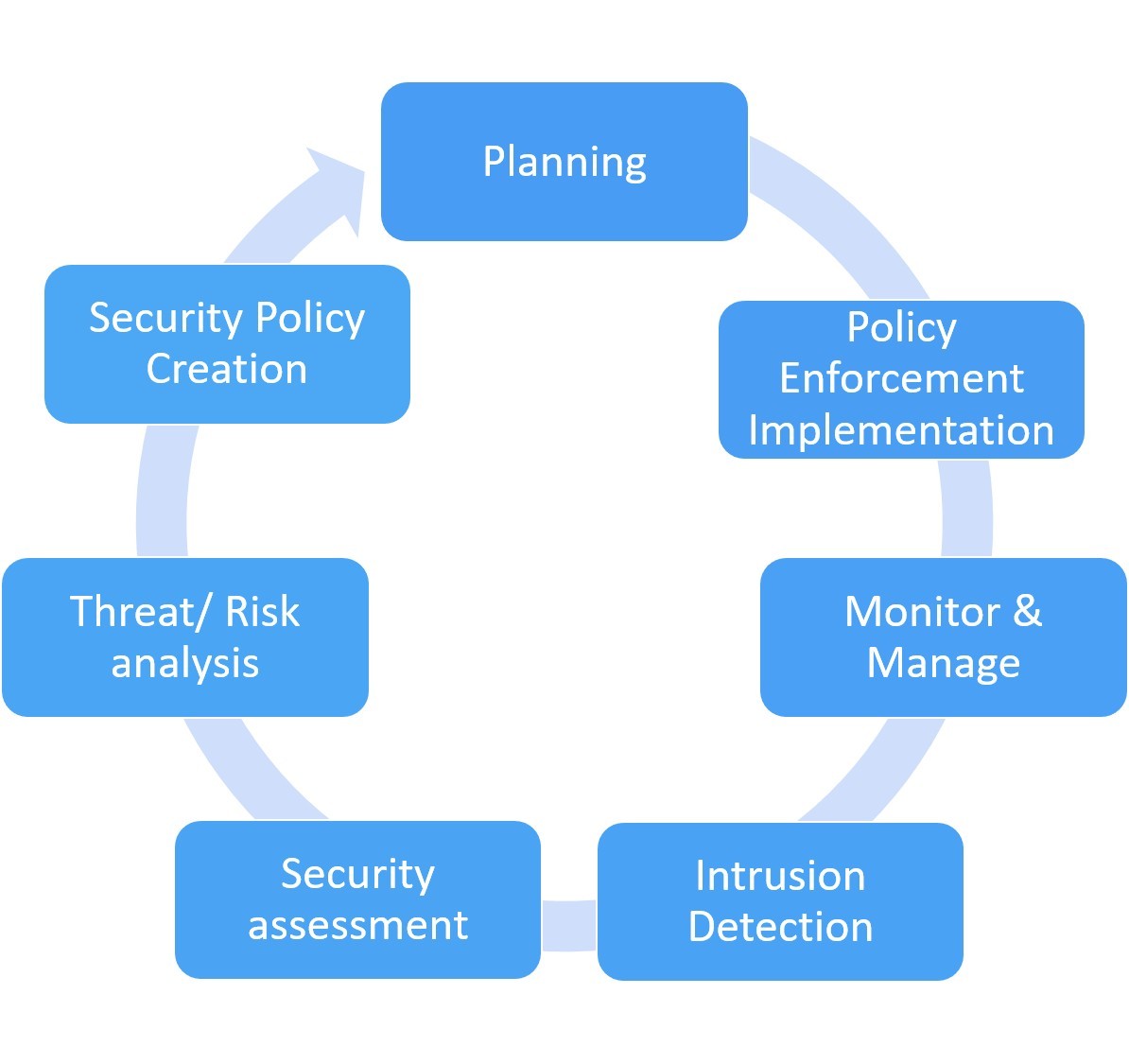
Cyber Security Advisory Services

Cyber Advisory Services
- Security & Risk Assessments
- Vulnerability Scanning
- Penetration Testing
- Log Configuration Review
Cyber Security Incident Response Plan
- CSIRP Creation & Testing
- Gap Analysis Services
- Capability Analysis
Information Security Policy Creation
Security Awareness Training
Application Code Review
Remediation Implementation
Project Overview
Cyber Security Audit and Recovery for Compromised Large Public Sector Organization
Scope of Work
- Investigate the affected systems to determine the level of compromise, affected areas and attack vectors
- Decide if the investigated system is safe to use
- Prioritise subsequent activities
- Data Collection
- Identify Data Sources
- Acquiring the Data
- Examination
- Analysis
- File Data Analysis
- OS Data Analysis
- Network Data Analysis
- Application Data Analysis
- Detection and Analysis
- Attack vectors
- Incident symptoms
- Reporting
- Recommendations
Project
Environment
- Microsoft
- RedHat
- Ubuntu
- Oracle Linux
- Cloud Infrastructure with 60 virtual machines
Tools
- Kali Linux
- Lynus
- OpenVAS
- RKHunter
- Proprietary Scripts
Project Duration
- 3 months
Project Team
- 3 Senior Linux Cyber Security Consultants
- 5 Senior Windows/ Microsoft Cyber Security Consultants
Next Steps
- Implement the Linux remediation plan as per the recovery plan
- Support the rebuild or implant removal as defined by the recovery plan
- Documentation
Project Overview
Cyber Security Audit and Recovery for Compromised Large Education Institution
Scope of Work
- Investigate the affected systems to determine the level of compromise, affected areas and attack vectors
- Decide if the investigated system is safe to use
- Prioritise subsequent activities
- Data Collection
- Identify Data Sources
- Acquiring the Data
- Examination
- Analysis
- File Data Analysis
- OS Data Analysis
- Network Data Analysis
- Application Data Analysis
- Detection and Analysis
- Attack vectors
- Incident symptoms
- Reporting
- Recommendations
Project
Environment
- Microsoft
- RedHat
- Ubuntu
- Oracle
- Cloud Infrastructure with 1,300 virtual machines
Tools
- Kali Linux
- Lynus
- OpenVAS
- RKHunter
- Proprietary Scripts
- Puppet
- Satellite
Project Duration
- 6 months
Project Team
- 5 Senior Cyber Security Linux Consultants
- 7 Senior Cyber Security Windows Server Consultants
Next Steps
- Implement the Linux remediation plan as per the recovery plan
- Support the rebuild or implant removal as defined by the recovery plan
- Documentation
Seems like a right fit? Get in touch with our experienced Consultants
